Wireshark is a popular network protocol analyzer tool that allows users to see what is happening on their network at a microscopic level. It is used by network administrators and security professionals to troubleshoot network issues, examine network traffic, and protect against security threats. While Wireshark has many advantages, it also has some disadvantages that users should be aware of.
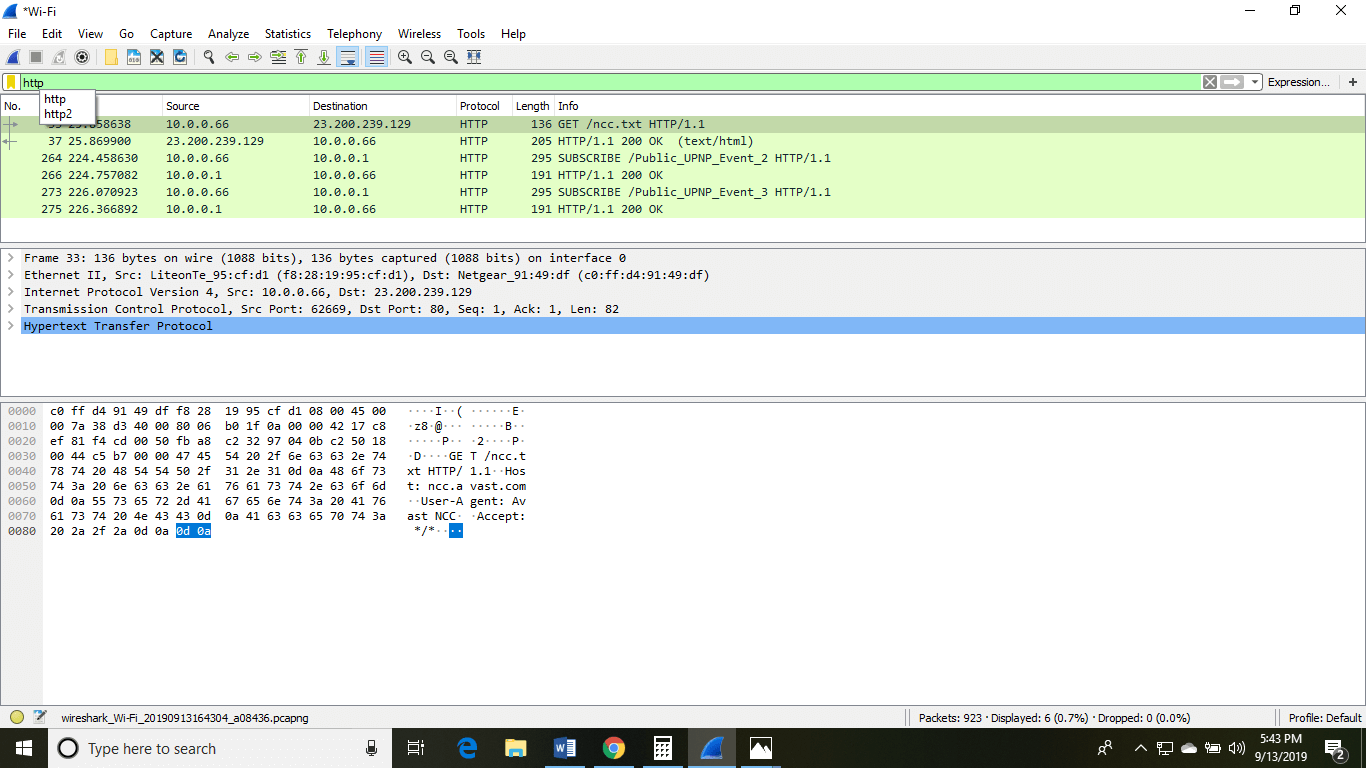
One of the biggest advantages of Wireshark is its ability to capture and display a wide range of network protocols. Wireshark can decode and dissect more than 1,000 protocols, making it an extremely powerful tool for analyzing network traffic. It also has a user-friendly interface that allows users to easily navigate through captured packets and view detailed information about each packet.
Another advantage of Wireshark is its ability to capture packets in real-time. This is particularly useful for troubleshooting network issues, as it allows users to see what is happening on the network as it happens. Wireshark also has a number of built-in filters that allow users to focus on specific packets or protocols, making it easier to identify and analyze specific traffic patterns.
One disadvantage of Wireshark is that it requires a certain level of technical knowledge to use effectively. While the user interface is fairly intuitive, understanding how to interpret the captured packets and apply filters can be challenging for those who are not familiar with network protocols and packet analysis. In addition, Wireshark can be resource-intensive, particularly when capturing large amounts of traffic, and may not be suitable for use on systems with limited resources.
Another potential disadvantage of Wireshark is the security risk it poses. Since Wireshark allows users to capture and view network traffic, it can potentially be used by malicious actors to capture sensitive information, such as passwords and login credentials. To mitigate this risk, it is important for users to ensure that Wireshark is properly configured and used only on secure networks.
In conclusion, Wireshark is a powerful and widely-used tool for analyzing and troubleshooting network issues. While it has many advantages, it also has some disadvantages that users should be aware of, including the need for technical knowledge and the potential security risks it poses. Properly configured and used in a secure environment, however, Wireshark can be an invaluable tool for network administrators and security professionals.