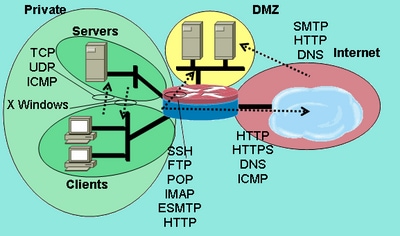
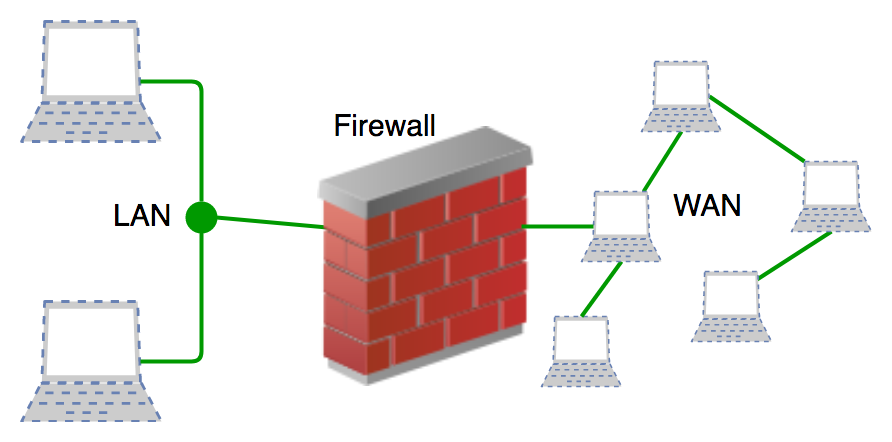
A zone-based firewall is a network security system that controls inbound and outbound network traffic based on predetermined security rules. It operates by dividing a network into different zones, with each zone representing a specific level of trust. The firewall then enforces rules that allow or deny traffic between zones based on the level of trust associated with each zone.
One common use of a zone-based firewall is to separate a trusted network, such as a corporate network, from an untrusted network, such as the Internet. In this case, the corporate network would be designated as a trusted zone, while the Internet would be designated as an untrusted zone. The firewall would then enforce rules that allow traffic to flow freely between the trusted and untrusted zones, while denying traffic between the untrusted zone and any other trusted zones.
Another common use of a zone-based firewall is to segment a network into different areas, each with its own level of security. For example, a company may have a public-facing network for customers, a private network for employees, and a secure network for sensitive data. In this case, the firewall would enforce rules that allow traffic to flow freely between the public and private networks, while denying traffic between the private network and the secure network unless it meets certain security criteria.
One of the key advantages of a zone-based firewall is its ability to provide granular control over network traffic. Because the firewall enforces rules based on the source and destination zones, it can be configured to allow or deny specific types of traffic based on the needs of the network. This allows administrators to implement fine-grained security controls that are tailored to the specific needs of their organization.
Another advantage of a zone-based firewall is its scalability. Because the firewall operates at the network level, it can easily be configured to protect large networks with multiple zones and subnets. This makes it an ideal solution for organizations with complex network environments that require flexible and customizable security controls.
In summary, a zone-based firewall is a powerful tool for securing networks by controlling inbound and outbound traffic based on predetermined security rules. It allows administrators to implement fine-grained security controls and is well-suited for large, complex network environments.
ZoneAlarm
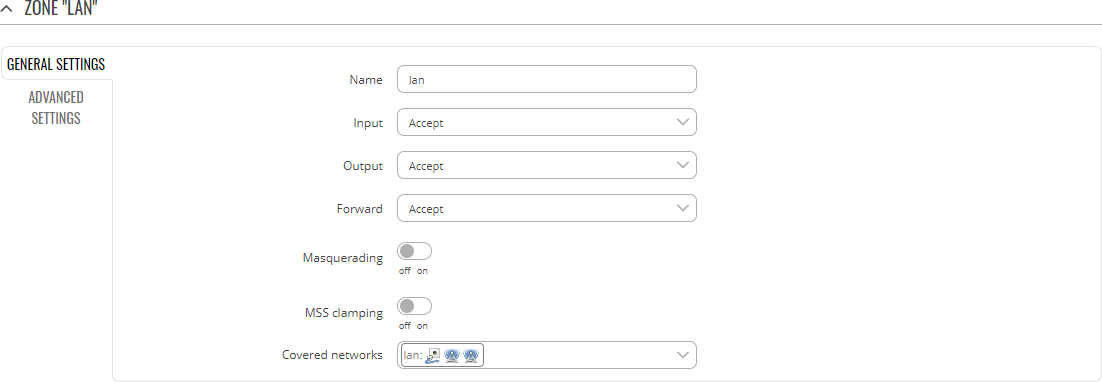
A policy package is a set of policies that you can install on a firewall, containing all the sets for each pair of zones. Besides explaining what is a firewall and how does it work, we will see what happens inside the firewall. You can attach policy maps to a target zone pair. To activate the platform inspect match-statistics per-filter command, re-apply all service-policies. If match protocol TCP is configured first, it will create issues for services such as FTP and TFTP and for multimedia and voice signaling services such as H. Similarly, when the response comes back from outside NAT, the source address will be 209.
Cisco IOS Zone Based Firewall Configuration Example (ZBF)
FIREWALL config class-map type inspect match-all VM-HTTP-TRAFFIC FIREWALL config-cmap match access-group name VM-TO-ANY FIREWALL config-cmap match protocol http FIREWALL config-cmap exit FIREWALL config class-map type inspect match-all VM-HTTPS-TRAFFIC FIREWALL config-cmap match access-group name VM-TO-ANY FIREWALL config-cmap match protocol https FIREWALL config-cmap exit More efficient approach is to use a nested class-map which will either match HTTP or HTTPS Boolean OR. However, Layer 7 inspection, as mentioned, requires a better understanding of network activity, as Layer 7 protocols that are not configured for inspection are not allowed between zones. According to our scenario, hosts in Inside zone must ping hosts located in outside zone, but hosts in outside zone will not be able to ping hosts located in inside zone. The type of information following the basic IPv6 header can be a transport-layer packet, for example, a TCP or a UDP packet, or an extension header. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Note: You only need to configure the servers-clients zone pair at present in order to inspect connections sourced in the servers zone that travel to the clients zone, shown next: configure terminal zone-pair security servers-clients source servers destination clients service-policy type inspect servers-clients-policy This completes the configuration of the user-defined inspection policy in the servers-clients zone-pair to allow X Windows connections from the server zone to the client zone. This is possible and can be easily verified.
Cisco Content Hub

No No Professional Windows 2000, Windows XP, Windows 2003, Windows Vista, Windows 2008. The firewall is still reachable NORTH ping 10. What do you find most challenging in that? For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. The following example shows the issue:! As the result, you can override no-communication rule between zoned and non-zoned interfaces. Application inspection policies are applied at Layer 7 of the OSI model, where user applications send and receive messages that allow the applications to offer useful capabilities.