IPv4 (Internet Protocol version 4) is the fourth version of the Internet Protocol (IP), a networking protocol used for transmitting data across the internet. It is the most widely used version of IP and is still in widespread use today, although it is being gradually replaced by the newer and more secure IPv6 protocol. Despite its widespread use, IPv4 has several security vulnerabilities that can be exploited by malicious actors.
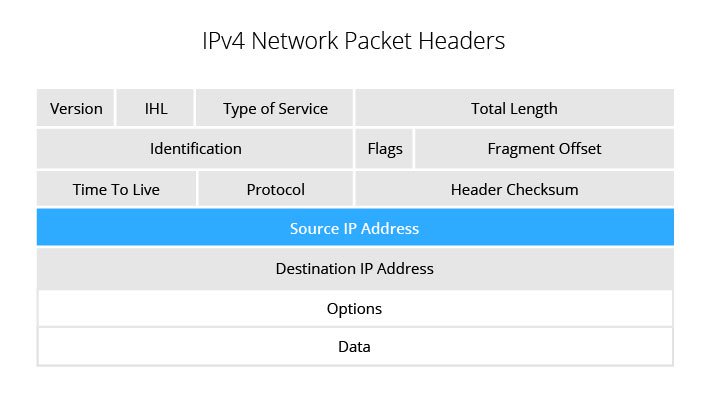
One of the main vulnerabilities of IPv4 is its limited address space. IPv4 uses 32-bit addresses, which means there are only about 4.3 billion unique addresses available. This may seem like a large number, but it is not enough to accommodate the growing number of devices that are connected to the internet. As a result, IPv4 addresses are often recycled or shared, which can create security risks. For example, if a device with a recycled IPv4 address is compromised, it can be used to launch attacks on other devices using the same address.
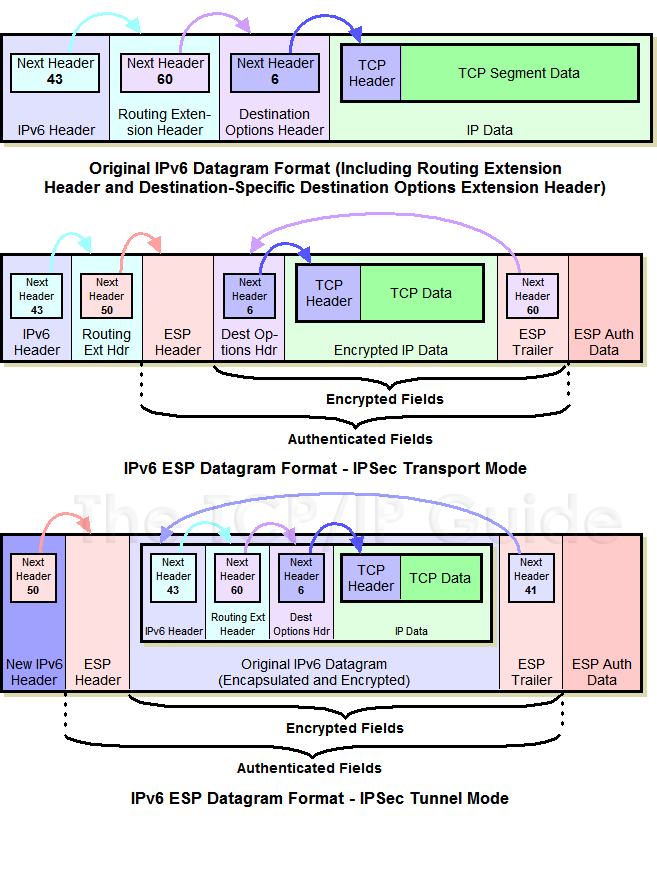
Another vulnerability of IPv4 is its lack of built-in security measures. IPv4 does not have any built-in encryption or authentication, which means that data transmitted over IPv4 networks can be easily intercepted and read by anyone who has access to the network. This makes it easy for malicious actors to steal sensitive information or launch attacks on other devices on the network.
To mitigate these vulnerabilities, many organizations and individuals use additional security measures such as firewalls, virtual private networks (VPNs), and network access control (NAC) systems to protect their networks and devices. These measures can help to prevent unauthorized access to networks and devices and can also detect and prevent attacks.
In conclusion, while IPv4 is still widely used and plays a crucial role in the functioning of the internet, it has several security vulnerabilities that can be exploited by malicious actors. It is important for organizations and individuals to take steps to secure their networks and devices, and to consider transitioning to the more secure IPv6 protocol as it becomes more widely available.