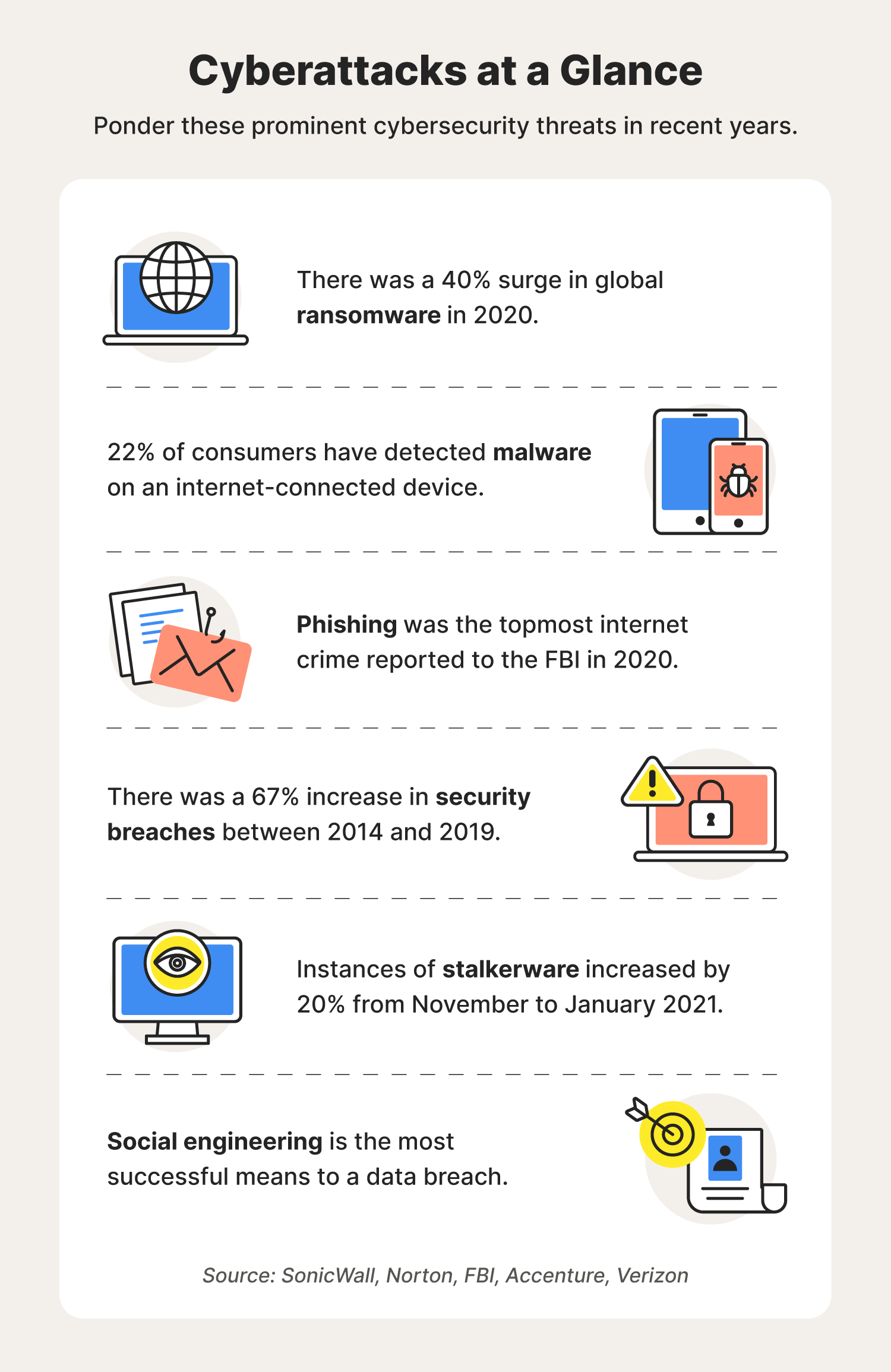
Phishing and pharming are two types of cyber attacks that are designed to trick people into divulging sensitive information, such as login credentials or financial details. These attacks can be highly effective because they rely on social engineering techniques to manipulate people into believing that they are interacting with a legitimate source. In this essay, we will explore some examples of phishing and pharming to better understand how these attacks work and how to protect ourselves from them.
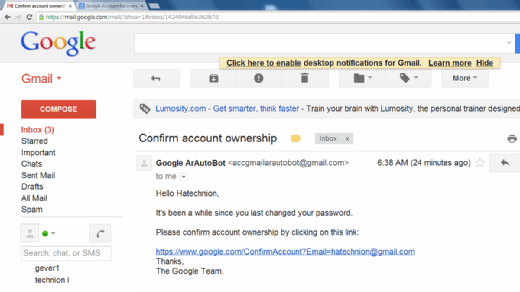
One common example of phishing is the use of fake emails that purport to be from a legitimate organization, such as a bank or government agency. These emails may contain links that, when clicked, lead to a fake website that is designed to look like the real thing. The goal of this type of phishing attack is to convince the victim to enter their login credentials or other sensitive information, which can then be used by the attacker to gain access to their accounts.
Another example of phishing is the use of fake social media profiles or messaging apps to send messages that appear to be from a friend or colleague. These messages may contain links or attachments that, when clicked or downloaded, install malware on the victim's device. This malware can then be used to spy on the victim or steal their sensitive information.
Pharming is a type of cyber attack that involves redirecting traffic from a legitimate website to a fake one. This can be done through a variety of means, such as compromising a Domain Name System (DNS) server or using malware to alter a victim's host file. Once the traffic has been redirected, the victim is presented with a fake website that is designed to look like the real thing. The goal of this attack is to convince the victim to enter sensitive information, such as login credentials or financial details, which can then be used by the attacker.
One example of pharming is the use of a fake e-commerce website to steal credit card information. A victim may be redirected to the fake website when they attempt to make a purchase on a legitimate e-commerce site. The fake website may look almost identical to the real one, making it difficult for the victim to realize that they are on a fake site. If the victim enters their credit card information and submits their order, the attacker can then use this information to make unauthorized purchases or sell it to other criminals.
In conclusion, phishing and pharming are two types of cyber attacks that rely on social engineering techniques to manipulate people into divulging sensitive information. These attacks can take many forms, from fake emails and social media profiles to fake websites, and can have serious consequences for the victims. To protect ourselves from these attacks, it is important to be vigilant and skeptical of any unexpected or unfamiliar requests for sensitive information. This may include verifying the authenticity of emails and websites before entering login credentials or financial details, and being cautious when clicking on links or downloading attachments.